Extracting power data from a smart meter display
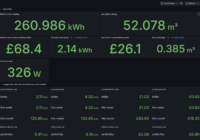
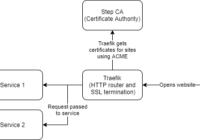
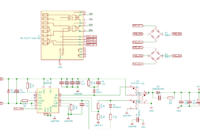
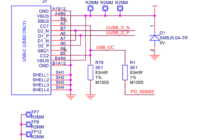
Recentely my electricity and gas meters were replaced with smart meters. I already had an energy monitoring system in place (originaly a openenergymonitor system but later modified to put data into grafana rather than their emoncms software). But with the new meters installed I wondered if their smart functionality would allow me to gather any… Read More »